Maxwell Strange
EDN
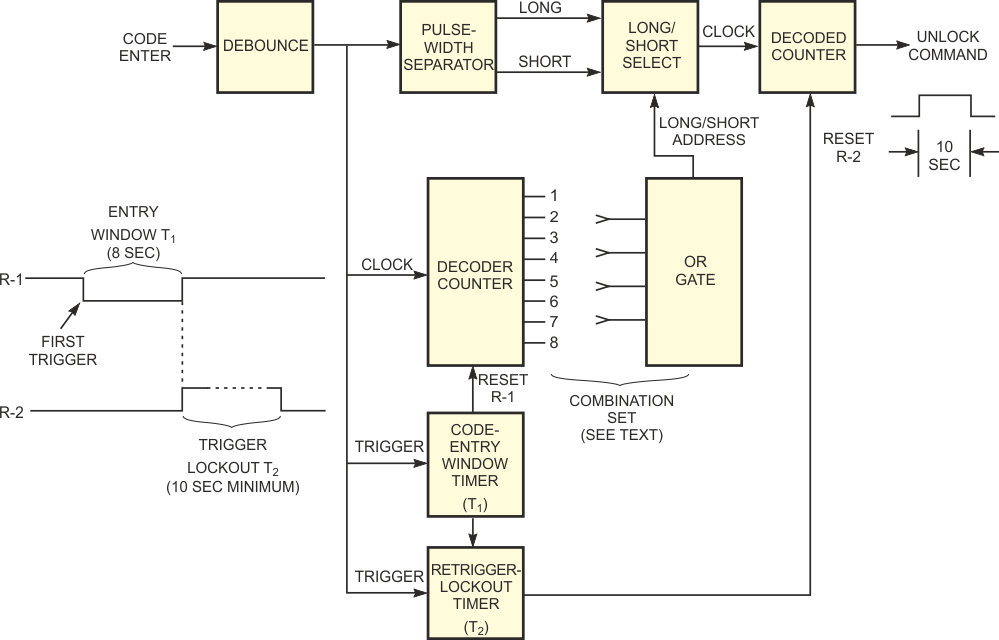
Figure 1 is the block diagram of an easily programmed, single-button combination lock. You operate the lock by using a series of short and long pulses from a momentary switch that masquerades as a doorbell button. The circuit uses inexpensive CMOS logic. The retriggerable timer, T1, locks out entries made after the T1 code-entry window, thereby greatly enhancing security. The circuit in Figure 2 operates as follows: The Schmitt-trigger quad NAND gate, IC1, debounces the code-entry switch and, with the aid of simple analog circuitry, produces separate outputs for activation times of less than and more than 0.3 sec. These outputs connect to the select gate, IC5. The initial entry also sets timer T1 to enable the decoded decade counter, IC3. Each entry clocks IC3.
 |
||
| Figure 1. | A handful of timers and counters configures a highly secure, single-button combination lock. | |
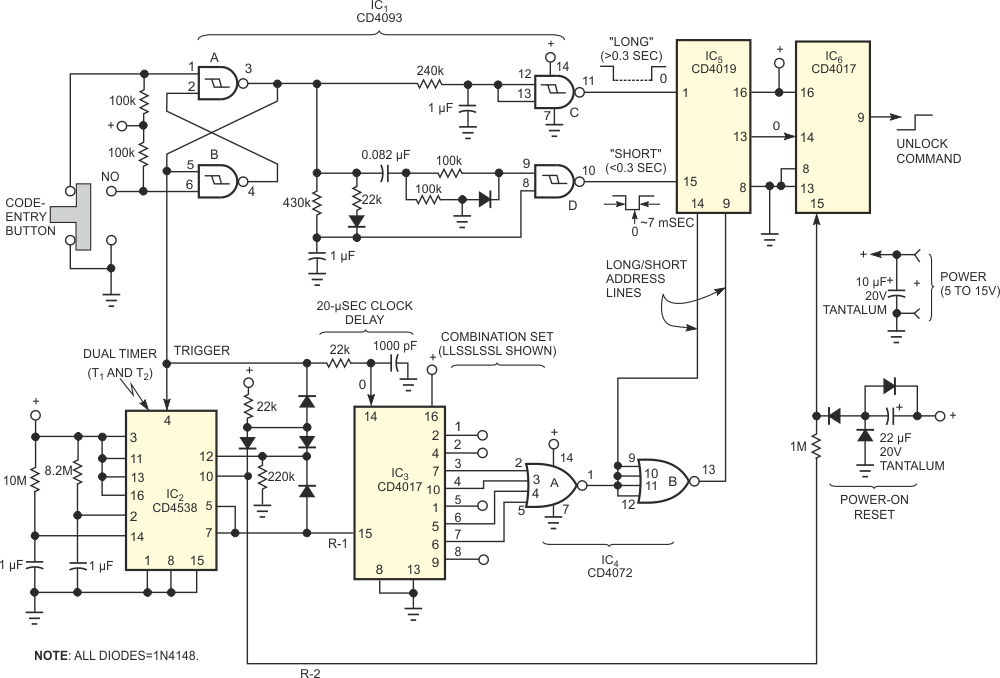
As IC3 steps through its counts, certain of its output positions represent "short" and connect to IC4's inputs; unconnected lines represent "long" positions. This coding arrangement sets the combination. Short pulse positions change the address of IC5 to select the short input pulse; otherwise, IC5 selects the long pulse input. The short and long inputs, if present in the programmed sequence, produce an output from IC5. IC6 counts the outputs and produces an unlock command only if it counts all pulses. The power-on-reset circuit ensures that no compromise of security arises under any conditions after a power outage. The timers are crucial to the high security of the system. You must enter the code within the 8-sec T1 window. If you make a mistake, you must wait at least 10 sec for T1 to time out before you make another attempt. If entries occur continuously and less than 10 sec apart, as an intruder might try, T1 continuously inhibits counter IC6.
 |
||
| Figure 2. | You program your combination by hard-wiring the IC3-IC4 output-to-input connections, LLSSLSSL, where L and S are long and short inputs, respectively, in this example. |
|
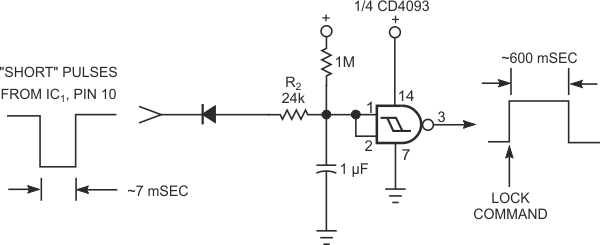
The lock proves to be reliable over several years of use. The circuit in Figure 2 uses an eight-character combination, which you can quickly enter. A short pulse is a quick jab to the button; a long pulse is only slightly longer. A shorter sequence would also be secure; you can implement a shorter code by simply taking the unlock pulse from a lower count on IC6. IC6's output returns low after 10 sec when T1 resets. If desired, you can generate a lock command, which need not be secure, by adding the simple circuit in Figure 3.
 |
||
| Figure 3. | You can generate a lock command with this additional circuit by rapidly entering four or more short pulses. | |