Soon, smart phones will include near-field communications (NFC) wireless technology so they can be used like keys or credit cards. Users simply wave their phone near an NFC reader, or tap it, and the devices exchange data to make a transaction. Automatic paring is another emerging application.
The Radio Technology
NFC’s maximum range is about 20 cm with a typical useful range of 4 to 5 cm, which benefits security. It uses the near field rather than the more familiar far field (see “What’s The Difference Between The EM Near Field And The Far Field?”).
The far field comprises the orthogonal electric and magnetic fields that extend out from the antenna beyond several wavelengths. The waves behave as Maxwell’s equations predict where the electric and magnetic fields exchange energy and rejuvenate one another along the signal path. The field strength decreases with distance (d) by a factor of 1/d2.
The near field is within one wavelength or less of the antenna. It also consists of an electric and magnetic field, although the magnetic field is more dominant. The signal strength drops off by a factor of 1/d6, making it far less useful.
Essentially, the near field is the magnetic field produced by the transmit antenna. It can be considered the primary of an air-core transformer, and the receive antenna can be seen as the secondary winding of that transformer. The attenuation makes the overall effective wireless range very short.
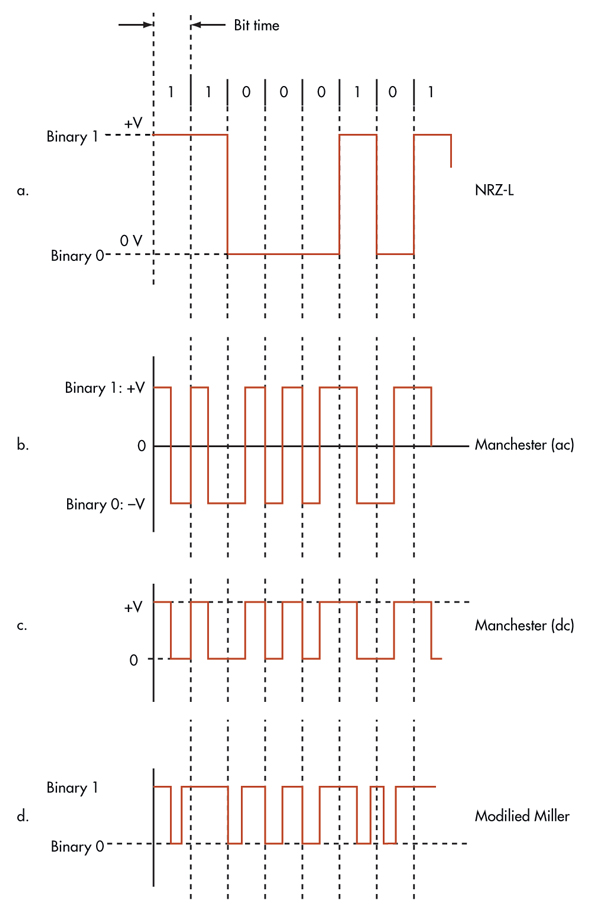
NFC operates on the unlicensed 13.56-MHz frequency. It is authorized in Parts 15 and 18 of CFR 47 from the Federal Communications Commission (FCC). Most other countries have authorized it as well. The modulation is amplitude shift keying (ASK) with either 10% or 100% modulation. The transmitted binary data uses either the Manchester code or a modified Miller code to ensure transmission reliability.
Data rates are 106, 212, or 424 kbits/s depending on the coding and modulation percentage. Some NFC devices use standard NRZ-L encoding. Binary phase shift keying (BPSK) modulation is an alternative at the 106-kbit/s data rate. Typical signal bandwidth is ±7 kHz or up to ±1.8 MHz depending on the data encoding and speed.
A data rate of 848 kbits/s is also available in some devices, but it is not part of the approved standards. A faster very high bit rate (VHBR) modification to the standard is under consideration and will boost the rate to 6.8 Mbits/s for some applications.
NFC Modes, Devices, And Protocols
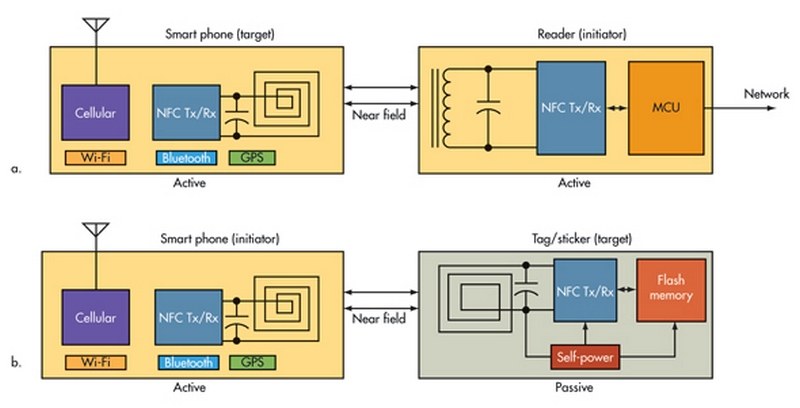
There are two basic operating modes for NFC: active and passive (Fig. 1). In the active mode, a battery or power supply fully powers both communicating devices. In the passive mode, one of the communicating devices is fully powered while the other is fully passive. The passive device, called a tag, derives its dc operating power from the receive RF signal transmitted by the active device.
Radio frequency identification (RFID) tags work the same way. The passive device powers up and transmits data back to the active device using load modulation, a form of ASK with a low modulation percentage. Load modulation has the data modulate an 848-kHz subcarrier that in turn modulates the main 13.56-MHz carrier. As a result, the signal varies the impedance of the listening device, which translates to a form of ASK.
Both the active and passive devices use Manchester coded 10% modulated ASK for both 212- and 424-kbit/s operation. Active devices use the Miller code and 100% modulated ASK for a 106-kbit/s rate to ensure an initial connection. Figure 2 shows the standard NRZ-L code and the NFC coding options.
The basic communications mode is half duplex, where one device transmits at a time while the other receives. The operation is “listen” before “talk.” One of the devices is an initiator that must listen on the channel and transmits only if no other signal is present. The initiator “polls” the other devices that may come near it. The other device, the target, listens and responds to the initiator according to a formal protocol.
Other modes of operation are read/write, peer to peer, and card emulation. Read/write operations are used to transmit data from one device to another with both active and passive devices. The initiator either reads or writes to a passive device. In the peer-to-peer mode, two active devices exchange data to establish a link for other transmissions. The card emulation mode works like an active device reading a passive device such as a smart credit card or tag.
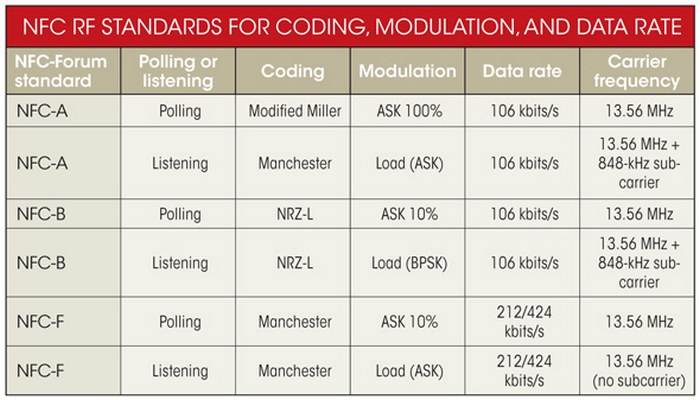
The multiple NFC standards, designated NFC-A, NFC-B, and NFC-F, define several slightly different transmission technologies. Each specifies a different data rate, modulation, coding, or operational mode (see the Table 1). The initiator polling device attempts to detect the specific mode of the responding device and then configures itself to the appropriate technology to complete the transaction.
Table 1. Multiple NFC standards specifies a different data rate, modulation, coding, or operational mode.
Also, the NFC standards define four basic types of passive tags from Type 1 to Type 4. Each type has a different memory capacity and matches one of the popular standards. Types 1 and 2 have 96- and 48- byte to 2-kbyte maximum storage and operate at 106 kbits/s. Types 3 and 4 run at 212 or 424 kbits/s and have either 1 Mbyte or 32 kbytes maximum, respectively.
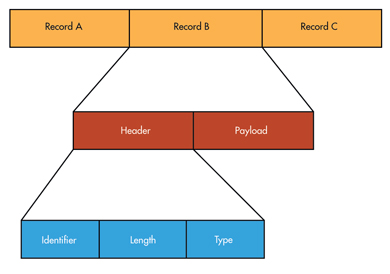
The NFC standards further specify a message encapsulation format called the NFC Data Exchange Format (NDEF) to use in the normal course of operation. Each transmission is called a message, and each message comprises one or more records (Fig. 3). A record includes the desired payload plus a defining header, which has identifier, length, and payload type fields. The payload is typically a URL or a data type defined by the standard NFC Record Type Definition (RTD) file.
|
|
|
| Figure 3. | Also called a message, the NFC Data Exchange Format (NDEF) comprises one or more records. A record includes the desired payload plus a header comprising identifier, length, and payload fields. |
NFC Standards
Most of the basic NFC standards were derived from RFID and smart card standards. They have become formal International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) standards, including those standards originally developed by participating companies:
- ISO/IEC 14443A (NXP, formerly Philips MIFARE)
- ISO/IEC 14443B (Infineon)
- JIS X6319-4 (Sony FeliCA)
The RF NFC standard is ECMA 340 (European Association for Standardizing Information and Communications Systems). It is designated NFCIP-1 or Near Field Communication Interface and Protocol. ISO/IEC adopted this standard as 18092. There is also NFCIP-2, called ECMA 352, and ISO/IEC 23917.
The NFC Forum (www.nfc-forum.com), a non-profit promotional group of companies, establishes and maintains a wide range of related specifications and standards related to NFC. It also provides testing and certification programs to promote interoperability of NFC devices. EMVCo, a joint business venture of Europay, MasterCard, American Express, and Visa, manages and maintains specifications for smart cards, point of sale (POS) terminals, ATMs, and related devices.
NFC Security
If NFC is to be used in lieu of credit card payments or access to critical facilities, the transmitted data must be secure. NFC has inherent security simply because its very short range prevents signals from traveling too far. However, that doesn’t mean NFC systems can’t be hacked. A high-gain directional antenna and sensitive receiver could eavesdrop on NFC signals at considerable distance, although the hacking receiver setup may not be that inconspicuous.
Security risks also come from other forms of hacking. For example, data corruption could occur when false data is transmitted to an NFC reader or other enabled device. Data also can be modified during transmission. During “man in the middle” attacks, hackers access the transmitted data and change it before retransmitting it. These attacks aren’t likely, but they are possible. The best way to protect the data from these forms of corruption is to encrypt or otherwise use techniques to secure the radio channel. Virtually all NFC radios are encrypted.
“Although NFC standards are already well defined and developed, additional progress is needed in point-of-sale infrastructure integration to fully realize the technology’s potential,” says Ron Vetter, IEEE Computer Society member and founder of Mobile Education LLC. “Because mobile payments will likely be the big driver for NFC, addressing customer concerns with security and privacy will also play an important role in how rapidly the technology is adopted.”
Next: Part 2